

The fan is good, but the orientation seems like it would struggle pushing air between the drives. Maybe a push-pull setup with a second fan?


The fan is good, but the orientation seems like it would struggle pushing air between the drives. Maybe a push-pull setup with a second fan?
My general attitude is similar to yours. Let OP figure out that the reporting and blocking is basically just creating more noise that has to gets filtered out and bot supply is basically infinite.
“It’s a learning experience.”
Good luck with that, I suppose. Botnets can have thousands, if not hundreds of thousands of infected hosts that will endlessly scan everything on the interwebs. Many of those infected hosts are behind NAT’s and your abuse form would be the equivalent of reporting an entire region for a single scan.
But hey! Change the world, amirite?
I don’t want to go so far as to tell you how to think, but as long as we are talking about how to visualize IP addresses, you may want to check out subnets and subnet masking.
The notation of IP addresses starts to make sense when you think about the early days of TCP/IP when all IP addresses were public and NAT’ing wasn’t really required yet. Basically, there needed to be ways for networks to filter traffic by IP blocks that were applicable. (It was [in part] a precursor to collision avoidance, but absolutely not the full story.) We still use addressing and masking today, but it’s more obvious when it’s local. (Like in data centers, where it’s super practical to mask off a block of addresses for a row or rack of servers.)
To your point, yeah. IP addresses are probably more comparable to the Dewey Decimal System rather than actual numbers and thinking of them as strings is probably easier.
255
Small correction, but an important one: 0 is a number too.
In terms of IP masking and broadcast addresses, the max is 255.255.255.255
For those who are still confused, ping works with 32 bit unsigned integers. While there certainly are more uses, it’s a much more convenient method for storing IP address in a database as it’s easier to sort and index than 4 numbers separated by 4 periods
http://www.aboutmyip.com/AboutMyXApp/IP2Integer.jsp?ipAddress=1.1.1.1
I would look into something like Doppler instead of Vault. (I don’t trust any company acquired by IBM. They have been aquiring and enshittifying companies before there was even a name for it.)
Look into how any different solutions need their keys presented. Dumping the creds in ENV is generally fine since the keys will need to be stored and used somehow. You might need a dedicated user account to manage keys in its home folder.
This is actually a host security problem, not generally a key storage problem per se. Regardless of how you have a vault setup, my approach here is to create a single host that acts as a gateway for the rest of the credentials. (This applies to if keys are stored in “the cloud” or in a local database somewhere.)
Since you are going to using a Pi, you should focus on that being a restricted host: Only run your chosen vault solution on it. Period. Secure and patch it to the best of your ability and use very specific host firewall rules for minimum connectivity. Ie: Have one user for ssh in and limit another user account to managing vault, preferably without needing any kind of elevated access. This is actually a perfect use case for SELinux since you can put in some decent restrictions on the host for a single app (and it’s supporting apps…)
If you are paranoid enough to run a HIDS, you can turn on all the events for any type of root account actions. In theory once the host is configured, you shouldn’t need root again until you start performing patches.


That’s what you just got shown: Shove the configgy bits into Git.
You will likely have to find the configs you want to save first.
Wustite, ferrous oxide, is black. FeO.
Typical rust, usually found as hematite, is Fe2O3 and is red/brown. Also an iron oxide.
Magnetite is also another black iron oxide, Fe3O4.
There are quite a few other flavors of iron and oxygen too.
Sorry if it sounded like my rant was directed at you as it absolutely wasn’t. Your comment triggered me, because I absolutely fully agreed with yours as well. ;)
setenforce 0 is much cleaner, I have found.
Its just complex
When a security mechanism becomes more complex to manage than what it is supposed to protect, it becomes a vulnerability itself.
If you had a minimal system that you built from the ground up yourself and wanted to only have that system function in very specific ways, SELinux would be perfect. I would go so far as to say it would be nearing perfection in some ways.
Sorry, but in the real world, ain’t nobody got time for that shit. If you use auto configuration tools or pre-canned configs for SELinux on a system you are unfamiliar with, it’s more likely to cause application issues, create security gaps and will likely be shut off by a Jr. admin who really has no fucking clue what he is doing anyway.
It’s just easier to keep your system patched and ensure basic network security practices anyway.
It’s not impossible to manage these days. In the early days it was, but most everything is automagic now. If I am not mistaken, SELinux can be enabled to ‘log only’ which would give you data better handled by a HIPS anyway. (Don’t quote me on that.)
You want me to do what now?

(Sudo, the cat.)
Everything else aside, my biggest gripes are with service control. Instead of just “service” they had to invent a new name that was super close to an existing function (systemctl vs sysctl) and reverse the switch order. (service sshd stop vs systemctl stop sshd.service)
Besides that, I absolutely hate that all the service configs are not in a standard location. Well, you get things like sshd.conf which are still in etc, but the systemctl configs are who knows where.
There are more important things to hate on with systemd, but I went for the superficial this time and I absolutely hate service management with systemd now.


Build a live boot USB for windows: https://monovm.com/blog/how-to-create-a-windows-live-usb/
There is a chance that the exe is just a wrapper for a compressed archive that contains the app to flash the bios and also the image. If the bios actually supports flashing manually, that would be super convenient.


Here is a start for you: https://www.msn.com/ko-kr/news/world/20년간-수류탄을-망치로-써온-할머니에-中-화들짝/ar-BB1oYj9a
It’s all Korean URL encoding in that link, btw. Here is a screenshot anyway.
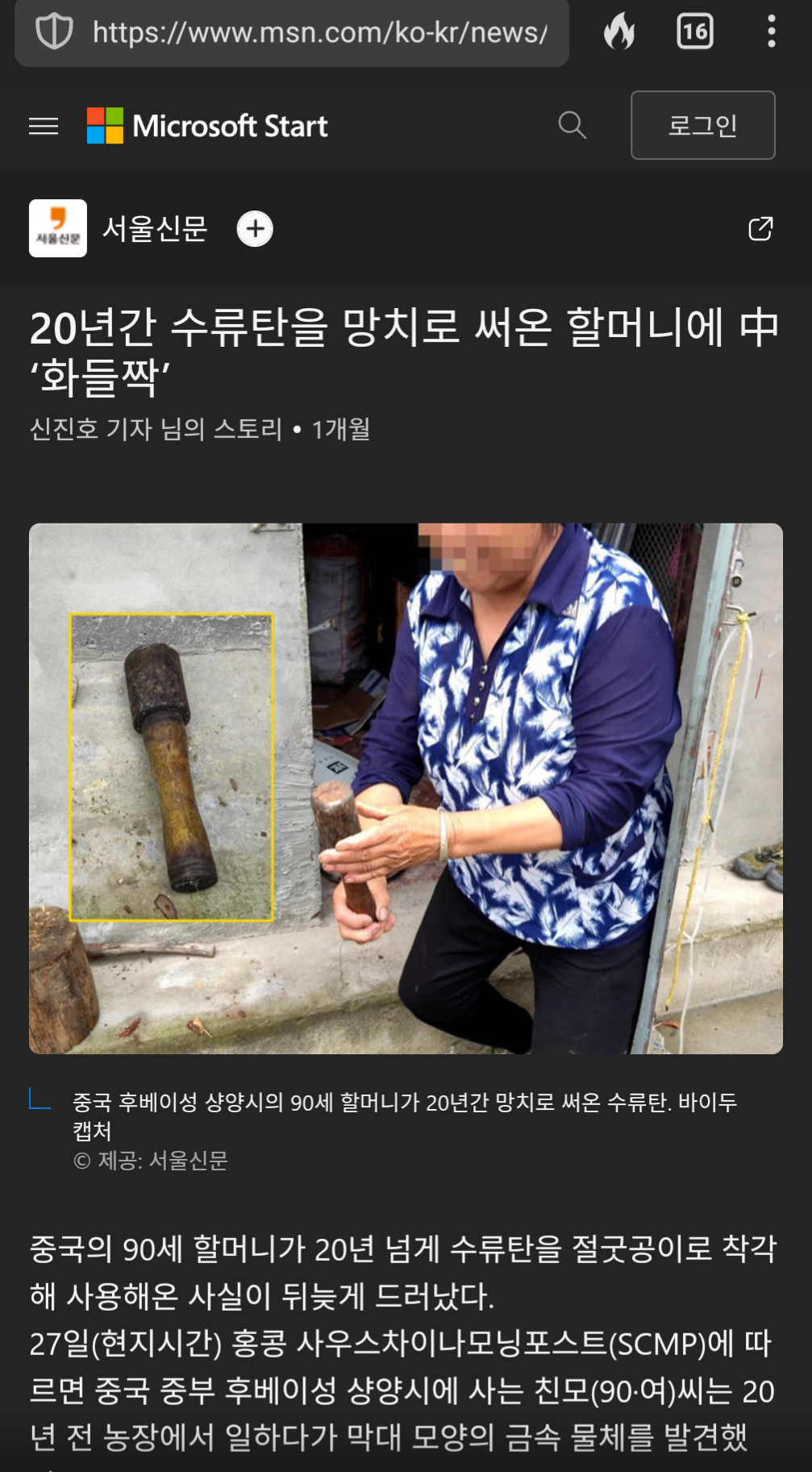


“Thanks, Steve!”
I think a conversation about Hannah Montana Linux could be quite entertaining.