

Keeping the source IP intact means you’ll have troubles routing back the traffic through host B.
Basically host A won’t be able to access the internet without going through B, which could not be what you want.
Here’s how it works:
On host A:
- add a /32 route to host B public IP through your local ISP gateway (eg. 192.168.1.1)
- setup a wireguard tunnel between A and B
- host A: 172.17.0.1/30
- host B: 172.17.0.2/30
- add a default route to host B wireguard IP
On host B:
- setup wireguard (same config)
- add PAT rules to the firewall so to DNAT incoming requests on the ports you need to 172.17.0.1
- add an SNAT masquerade rule so all outbound request from 172.17.0.1 are NATed with host B public address.
This should do what you need. However, if I may comment it out, I’d say you should give up on carrying the source IP address down to host A. This setup I described is clunky and can fail in many ways. Also I can see no benefits of doing that besides having “pretty logs” on host A. If you really need good logs, I’d suggest setting up a good reverse proxy on host B and forwarding it’s logs to a collector on host A.

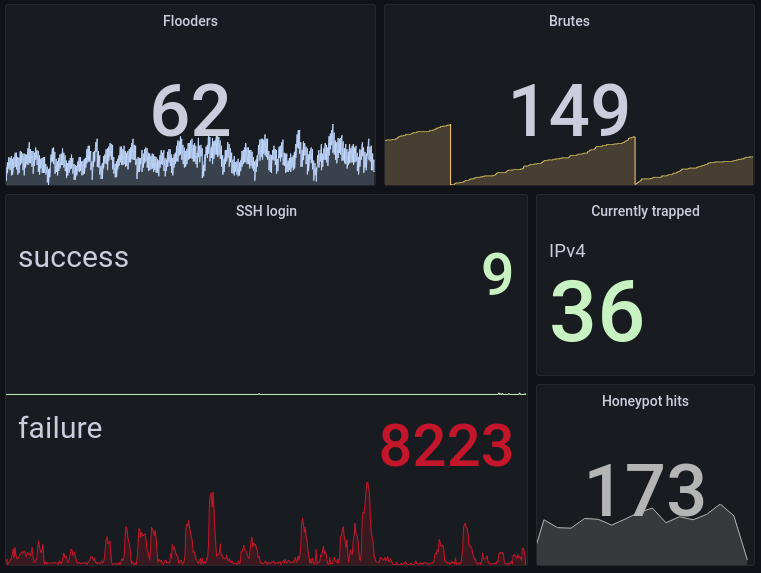
endlessh was pretty cool and a more modern version is even better ! I’ll give it a shot !
On a side note, I found a way to trap HTTP connections too while working on my cyb.farm project. The go implementation is ridiculously simple: tarpit.go. It works by providing an endless stream of custom headers to the client, which it is supposed to ingest before getting to the content itself.